Have you ever heard the saying “Don’t judge a book by its cover”? Well, in the world of digital advertising, it’s important to do just that! Domain spoofing, a crafty tactic cyber criminals use, makes it look like their website or app is legitimate, tricking advertisers into paying for ad space on a fake domain. These websites are your identical copy, so you not only lose on ad dollars but your readers are put at risk too.
Although advertisers and publishers suffer alike in the digital advertising landscape, the wounds are deeper for the publishers.
An advertiser can pause/cancel the underhand campaigns as soon as they know of the fraudulent activity. Next time, they tend to avoid the sites from the last campaign (blacklisting). On the other hand, a credible publisher will lose readers, advertisers, and some potential contributors, forever.
Of course, unless you’re Facebook or Google, it’ll be nearly impossible to regain the users and advertisers. Do you know what’s worse?
Mid-sized and small publishers are forced to battle against ad fraudsters without any advanced technologies (as they can’t afford one) and experience. Premium publishers have their own problems with ad fraudsters; most of the time, a premium is an ideal target for fraudulent networks.
With the rise of technology and digital ad budget, ad fraudsters have also evolved, and there are over 30 types of ad fraud today. Among these types, domain spoofing is the most common one. This article will delve into domain spoofing and provide actionable prevention tips. So, let’s get started!
Table of Contents
What Is Domain Spoofing?
In general, Domain spoofing is a type of cyber-attack where an attacker creates a fake website or email address that appears to be from a legitimate organization or individual. The goal of domain spoofing is usually to deceive the user into divulging sensitive information such as usernames, passwords, credit card details, or other personal data.
In the programmatic marketplace, domain spoofing is ad fraud involving a fraudulent website or app misrepresenting itself as legitimate. Spoofing a premium publisher makes the ad impressions more valuable, and the demand will also be typically high. This deceives advertisers into believing their ads are displayed on reputable websites. In domain spoofing, fraudsters manipulate the ad exchange to impersonate high-quality websites, allowing them to serve ads on low-quality sites, generating illegitimate profits for the fraudsters.
Domain spoofing is a significant problem in the digital advertising industry. It can deceive advertisers into believing their ads are being displayed on reputable websites, leading to wasted ad spend, damaged brand reputation, and lost revenue for publishers. It is a prevalent type of ad fraud and has become increasingly sophisticated, making it challenging to detect and prevent. Advertisers believe their ads are showing up on premium websites for the right audience. However, the fraudsters will show them up on low-quality websites for the bots (or, sometimes, a random audience).
Methbot, the most profitable ad fraud operation to date, has spoofed 250,267 distinct URLs to falsely represent inventory.
– WhiteOps
Generally, fraudsters build a domain that closely resembles the URL of legitimate publishers. Not only do they create fake domains, but they can also create duplicate copies of the website’s content.
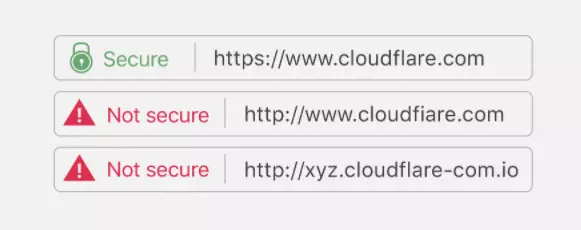
Domain Spoofing Examples
How Does Domain Spoofing Affect Publishers?
The Financial Times (FT.com) ran an audit in 2017 and found that FT.com had been spoofed, and fraudsters via these spoofed domains were selling display inventories on 10 ad exchanges and video ads on 15 exchanges. FT.com doesn’t sell video ads programmatically at all.
The money will never reach the publisher as the website is theirs. The publisher estimated the fraudsters were making over $1.3 million monthly, claiming they were the Financial Times.
Estimated Loss: $1.3 Million Per Month.
“The scale of the fraud we found is jaw-dropping. The industry continues to waste marketing budgets on what is essentially organized crime.”
-Anthony Hitchings, Digital Advertising Operations Director, The Financial Times (Src)
Similarly, News UK conducted a blackout test to measure the influence of fraudsters on its brand in 2018. In 2 hours, News UK found that around 2.9 million bids are made on domains pretending to be News UK titles (The Sun and The Times of London).
The publisher estimated that 650,000 ad requests were made each hour, and $950,000 was wasted monthly on the spoofed domains.
Estimated Loss: $950,000 Per Month.
“We’re all victims in one way or another. If the SSPs hadn’t taken it seriously, then it might have been different, but they were very keen to address it.”
-Ben Walmsley, Digital Commercial Director, News UK (Src)
How Does Domain Spoofing Work?
Domain spoofing can be done in several ways, but some of the most common methods include the following:
- Email spoofing: The attacker sends an email with a fake sender address that appears to come from a legitimate source. This can be done by manipulating the email header information, which is often easy.
- Website spoofing: The attacker creates a website that looks like a legitimate site, often by copying the design and content of the real site. They may also use a similar-sounding domain name or create a subdomain that looks like it belongs to the real site.
- DNS spoofing: The attacker can intercept traffic between a user and a legitimate website and redirect the user to a fake site. This is often done by modifying the Domain Name System (DNS) settings on the user’s device, router, or server.
- Man-in-the-middle attacks: In this scenario, the attacker intercepts traffic between a user and a legitimate website or email server and alters the data in transit or impersonates one of the parties to the communication.
In the programmatic marketplace, generally, domain spoofing works by compromising the ad exchange or ad network, or SSP. The domain spoofers capitalize on the ambiguity of real-time bidding and supply the spoofed URL instead of the legitimate one at the bid time.
What are the Different Types of Domain Spoofing?
Generally, there are four types of Domain spoofing:
- Malware
- Custom Browsers
- Cross-domain Embedding
- URL Substitution
Domain spoofing can be easy-to-detect and, sometimes, sophisticated enough to bypass vendors preventing ad fraud. Hence, it’s imperative to know how you can be tricked. Luckily, domain spoofing isn’t intractable, and you can deal with it one way or another.
Let’s start with the most common type of domain spoofing.
Malware
Fraudsters don’t need to corrupt the header information or ad tag to mess up the RTB. They can bug the real browsers by making the users download the malware abstractedly. For instance, you might have encountered a situation where you’ve been redirected (to a new window), and suddenly a software or file will start downloading automatically.
Not all redirects result in malware, but some are intended to bug the browser.
So, what happens then?
Fraudsters will keep on injecting ads into websites that the users view, and no, the money won’t end up in the publishers’ hands. If you are viewing the content on the New York Times, the malware can send out a bid saying we got an impression of the user from the nytimes.com and will indeed sell it for a lower-than-actual price.
Custom Browsers
RTB relies on the header information sent by the browser (up to an extent), and typically, advertisers get to know the sites being visited from that information. Spoofers take advantage of this and develop custom browsers that could copy the header information of the premium legitimate sites to capture the ad dollars. Ads will be served on random low-quality sites instead of the intended sites.
Cross-domain Embedding
Another simple approach used by fraudsters to spoof domains is nesting iframes. Suppose the fraudsters have two websites – one with high traffic and low-quality or non-brand-safe content and another with low traffic and high-quality or brand-safe content.
The fraudsters will nest iframes to show the ads to the low-quality site, while the advertisers bid for the high-quality content site. In other words, the parent domain is not where the ads are displayed. Instead, the nested domain (low-quality site) shows the ads to its readers and captures the ad dollars in the parent domain’s name.
URL Substitution
To make things worse, publishers occasionally reveal their domain ID and label of their site ID in the RTB ecosystem. Fraudsters use this opportunity to spoof the inventories and represent themselves as “forbes.com” (for example). Spoofers usually deceive advertisers by substituting the fake URL at the bid time by supplying a spoofed domain to the ad exchanges.
How to Detect and Stop Domain Spoofing?
Domain spoofing can significantly impact publishers, harming their brand reputation and wasting ad spend. However, with the right strategy, publishers can protect themselves and ensure their website is safe from fraud. Here are some recommendations to help publishers combat domain spoofing:
- Add Ads.txt:
Ads.txt is a simple text file that publishers can add to their root domain to offer greater control over the ads served by ad-tech partners. This file lists all the authorized sellers of the publisher’s inventory, making it easier for advertisers to verify that they buy ad space from a legitimate publisher.
- Partner with ad verification and measurement companies:
Ad verification and measurement companies like Integral Ad Science and WhiteOps can help publishers detect advanced types of domain spoofing. These companies use sophisticated tools and techniques to monitor and analyze ad traffic, identify fraudulent activity, and prevent it from impacting the publisher’s inventory.
- Reconcile bids and reported ad impressions:
Publishers should reconcile bids with the reported ad impressions to detect discrepancies. If the number of bids received is significantly higher than the number of ad impressions, it could indicate that domain spoofing is occurring. By monitoring these metrics, publishers can identify suspicious activity and take action to prevent it from harming their inventory.
- Work with trusted partners:
Publishers should work with trusted partners, such as ad networks and exchanges, with a track record of transparency and accountability. Publishers should also do their due diligence when selecting partners and ask for references and case studies to ensure they have a history of delivering quality inventory.
- Report suspicious activity:
If publishers suspect domain spoofing, they should report it to the appropriate parties, such as their ad network or exchange. They may be able to investigate and take action to stop fraudulent activity. Reporting suspicious activity can also help the industry as a whole to identify and combat fraud.
The Best Foot Forward
In digital advertising, domain spoofing can be a significant threat to publishers. It can damage brand reputation, waste ad spending, and harm the industry’s overall health. However, by implementing the right strategies and taking proactive measures, publishers can protect themselves against domain spoofing and ensure their website is safe.
Adding Ads.txt, partnering with ad verification and measurement companies, reconciling bids and reported ad impressions, working with trusted partners, and reporting suspicious activity are all critical steps in combating domain spoofing. By taking these measures, publishers can have confidence that their inventory is legitimate and that their brand reputation remains intact.
The digital advertising industry is constantly evolving, and publishers must stay on top of the latest trends and best practices. By staying informed and taking proactive measures, publishers can help ensure they put their best foot forward and build a sustainable and successful digital advertising business.
FAQs
Q1. What is domain spoofing?
Domain spoofing is a type of ad fraud where an illegitimate website falsely claims to be legitimate to serve ads and earn revenue.
Q2. How to prevent domain spoofing?
Publishers can prevent domain spoofing by adding Ads.txt, partnering with ad verification companies, reconciling bids and reported ad impressions, working with trusted partners, and reporting suspicious activity.
Q3. How to identify domain spoofing?
Publishers can identify domain spoofing by monitoring their ad inventory, reconciling bids and reported ad impressions, and working with ad verification and measurement companies to detect and prevent advanced domain spoofing types.