You know the story. The whole ad tech industry is trying to adapt itself to the changing consumer behaviors, privacy laws, and most importantly, function in a cookieless environment. Meanwhile, a few browsers like Mozilla are using the opportunity to grow their user base. In its attempt to gain some market share and entice users to switch, Mozilla has announced a new feature called Total Cookie Protection.
It is an addition to many other similar features that Mozilla has added to Firefox to present it as a privacy-centric browser. Specifically, Total Cookie Protection makes cross-site tracking even more difficult on the browser that already blocks a lot of trackers.
Table of Contents
What is Total Cookie Protection?
Total Cookie Protection is a new feature in Mozilla Firefox that limits the ad tech vendors to have a siloed access to the cookie. It’ll directly impact cross-site tracking on the browser. It is Mozilla’s one of the many attempts to make user tracking difficult in the open web.
“In our ongoing commitment to bring the best innovations in privacy, we are working tirelessly to improve how Firefox protects our users from tracking.”
– Mozilla
The Case of the Cookies
A browser holds multiple forms of data to provide a user-friendly experience on websites. A cookie is one of the tools that allow the browser to maintain and utilize the required data like log-in details, site preferences, etc. A cookie also holds the data that is needed to serve the right ads to the users. Mozilla categorizes the cookie as a stateful API because its state persists despite reloads, navigations, and browser restarts.
Browsers generally allow cookies to be read by the originator no matter whether it is doing so as a first-party or a third party. For example, Facebook can cookie a user on Facebook.com. The company can not only access the cookie as a first-party when the user is on its site but it can also retrieve it when the user is on TheGuardian.com if the news publisher has Facebook’s code on the site (via any embeds).
In this way, Facebook can consistently serve the most relevant ads even when the user is visiting different sites because of its ability to add and retrieve cookies.
What does Total Cookie Protection change?
Total Cookie Protection is based on a mechanism called State Partitioning. It means Firefox will partition the cookie storage and the access to the storage will be limited, resulting in lesser relevant ads.
The originator wouldn’t be able to access the cookie in the same way as earlier. Its access rights will depend on the site that the user is visiting. Every website will have a dedicated storage bucket. The data generated by a user on a site will remain inside the bucket dedicated to it. So, when a third party is delivering ads to a user on a site, it’ll have access only to the data which is inside the bucket of that site.
How does it work?
When browsers like Firefox want to stop the trackers, they simply block third parties from accessing the cookie. But State Partitioning takes a different approach. It provides embedded resources with a separate storage bucket for every site.
Before:
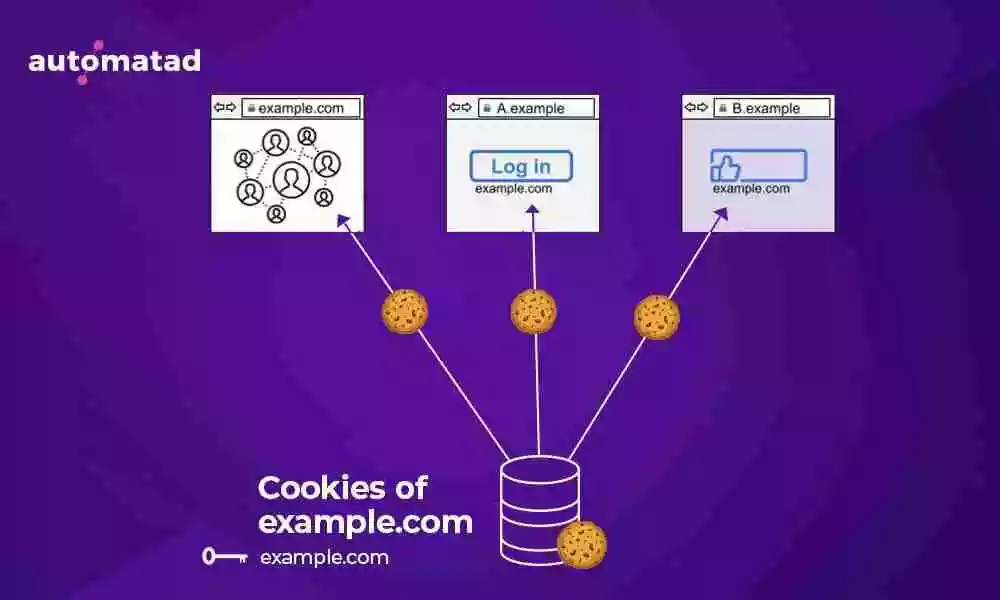
Without Total Cookie Protection, Facebook could store a cookie in your browser when you visit Facebook.com and it could access and use data from that cookie — even on other sites where it is present as embedded resources (ex: Facebook Comment).
For example, if you visit The Guardian and it has embedded Facebook comments on its posts, then Facebook can access its original cookie to store more information and use the ID to deliver highly relevant ads on The Guardian or any other site you visit.
So, Facebook has a single cookie bucket to store your information and use the same as you browse the web.
After:
But, with the new update, Facebook Comment on The Guardian will have a separate cookie bucket — associated with The Guardian. This storage is keyed to the top-level domain (theguardian.com) and completely partitioned from Facebook.com’s cookie bucket.
In a line, third-party will have a different cookie bucket tied to the domain that the user is visiting. So, no third parties can use their own cookie to track the users across the web.
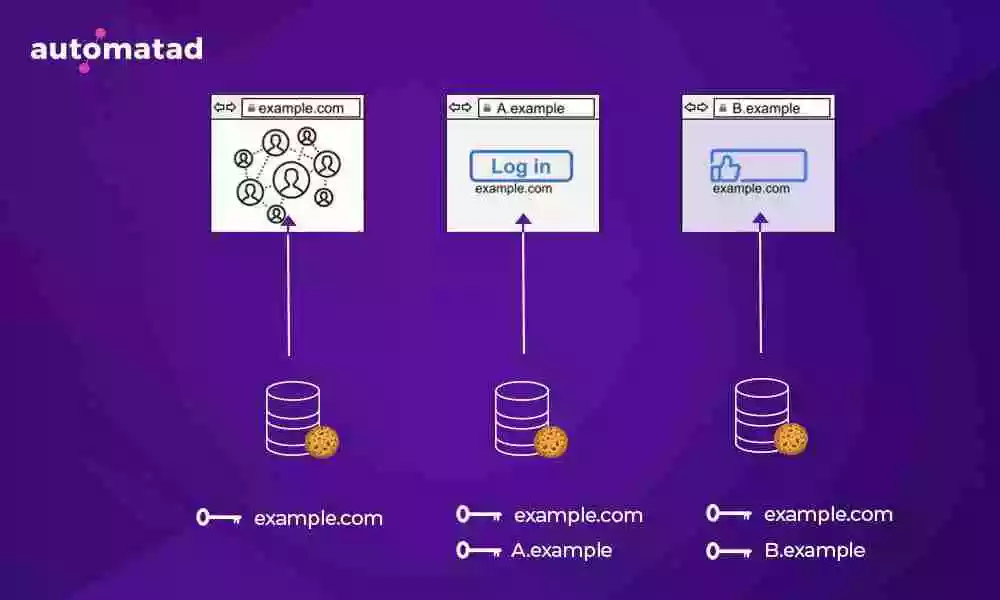
Example.com has three different cookie buckets to store cookies. The first one is used when users visit example.com and the second one is used when users visit a different site A.example (example.com is a third-party here) and the third one is used when users visit B.example (example.com is a third-party here).
As all three buckets are partitioned from one another, example.com can’t use the identifier/data from its own site when the user is on any other site (A.example, B.example, etc.)
Exceptions in Total Cookie Protection
Can Total Cookie Protection break single sign-on?
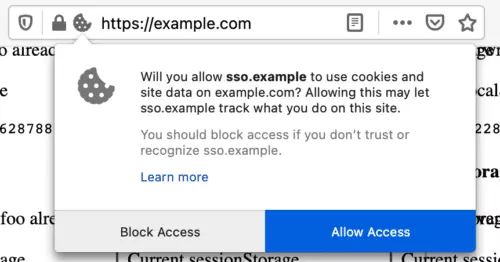
With Total Cookie Protection, Firefox tries not to block third-party cookie usage when it is required for site usability. For example, partitioning will not happen in the case of single-sign-on services. Both, the website and the service will access the same cookie jar as earlier so that the user can sign inconveniently. In some cases, the user has to allow access via a prompt for permission. Firefox will remember the user’s preference for 30 days.
Also, the third parties will have unpartitioned access only on the site where the user has allowed it. For example, say the user has allowed so. example to use the cookie and signed in to example.com, but it doesn’t mean that sso.com got the same permission for all the sites the user visits from here. If sso.com provides signing-in to another site, say example2.com, it’ll have to take the permission once again.
Total Cookie Protection vs Enhanced Tracking Protection
To block cookies, Mozilla Firefox already has Enhanced Tracking Protection in place. The Total Cookie Protection is an addition to ETP. The Total Cookie Protection also tries to eliminate a shortcoming of ETP.
Is Total Cookie Protection better than Enhanced Tracking Protection?
The Enhanced Tracking Protection feature relies on a list of trackers maintained by a company named Disconnect. Every tracker in the list was blocked by the ETP. So, the efficiency of the feature depended completely on how updated the list is. The Total Cookie Protection feature doesn’t need the list.
How does it affect you?
Some of the Firefox visitors can yield a lower return on your site due to weaker targeting. We said ‘some’, because not every user will have the feature turned on. Firefox users have to enable Total Cookie Protection by going into the security settings of the browser. So a small subset of the users of a browser that has around 8% market share, shouldn’t have a considerable impact on your revenue.
Even if the odds are not in your favor and this feature starts causing great losses for you, soon ad tech companies will stop using the cookie as an identifier.
What’s Next?
As we said,
Should publishers be worried about Total Cookie Protection?
you’ll most likely, remain almost unaffected by this feature. It’s better to prepare for the bigger challenge, i.e. the end of the cookie. If you are a publisher with first-party data, neither the updates like Total Cookie Protection nor the depreciation of the cookie should be an issue for you. So, invest your resources in building your first-party data strategy.
You should also keep a tab on ID solutions, they are rising up as an alternative to cookies but we have to wait to know how effective they can be.