3ve was one of the most sophisticated ad fraud operations witnessed by the adtech industry, siphoning over $29 millions from the ecosystem. Tag evasion is one of the techniques used by 3ve operators to avoid detection.
In here, we’re going to explore what is tag evasion and how can you prevent yourself from being a victim of such schemes in the future.
In case you’re wondering whether you should care about this rare, lesser-known technique, 3ve counterfeited 10k+ websites and such operation could raise again replicating the same techniques (citing the success of the first one).
Before getting any further, you need to know about 3ve. 3ve was one of the complex ad fraud operations dismantled by White Ops and Google in 2018. Eight persons related to the operations were indicted by the DOJ and it had three sub-operations working parallelly to spoof domains, fake impressions, and sell bot traffic.
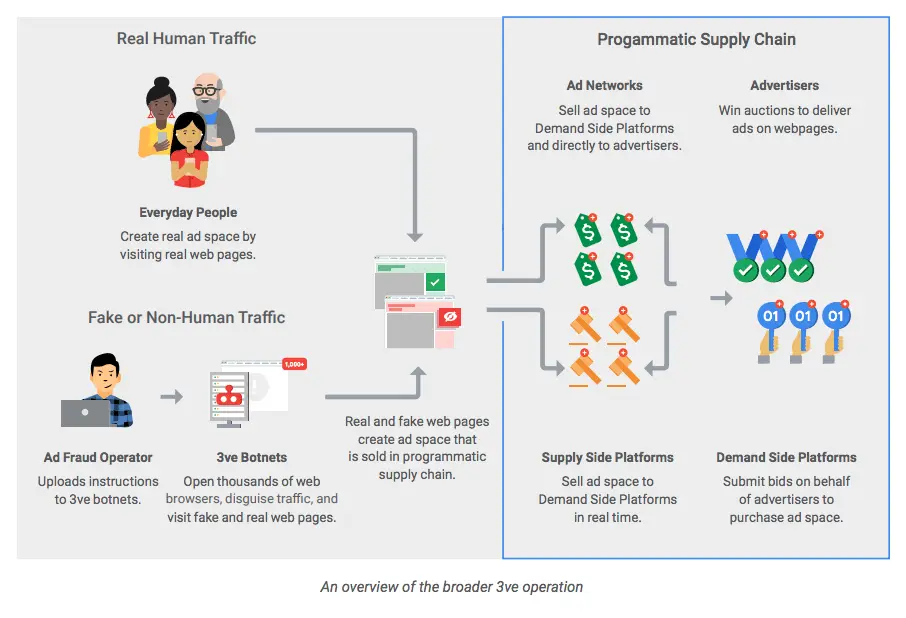
Of three, 3ve.2 is a botnet operation designed to sell fake inventories and dodge ad fraud detection by ‘tag evasion’.
Table of Contents
What is tag evasion?
Tag evasion, as the name implies, is a technique used by ad fraudsters to block ad fraud detection or any other unwanted scripts from executing or rendering. If the scripts aren’t executed, you can’t detect the presence of ad fraud with the tools.
Your ad fraud detection tags wouldn’t get a request (HTTP GET) let not execute.
How Does Tag Evasion Work?
Let’s take the 3ve as an example and see how Tag Evasion works. 3ve used two techniques to evade tags.
- Regular expression matching technique: 3ve.2 used a regular expression (regex) matching technique to find and replace the unwanted assets on the page with “none” so that the script won’t be executed at all.
- String blacklist: This sub-operation used another method to evade the tags. String blacklist was created based on the resources found in the list of blacklisted strings (in 3ve, it’s called bbb_j_m c2 variable).
Brief Explanation:
1. Regular expression matching technique:
3ve.2 used a regular expression (regex) matching technique to find and replace the unwanted assets on the page with “none” so that the script won’t be executed at all.
Technically, when a website loaded, the malware went through every URL in the site and pushed them to a function. The function compared URL against a preset regex to determine whether a resource should be loaded or blocked. White Ops said the same regex technique has been used to block its own JavaScript tag.
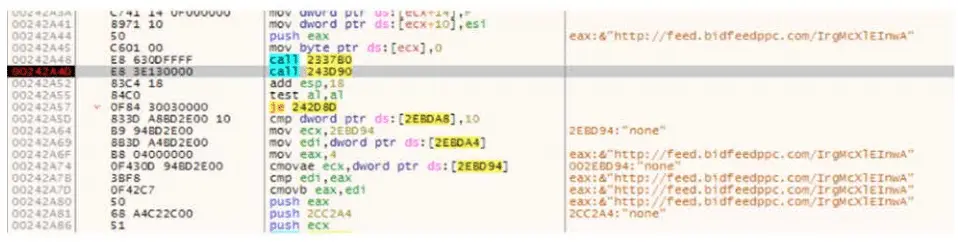
If the regex expression found a match, the function would return 1 and the resources will be blocked. If there’s no match, the function would return 0, thereby allowing the resources to render customarily.
2. String blacklist:
This sub-operation used another method to evade the tags. String blacklist was created based on the resources found in the list of blacklisted strings (in 3ve, it’s called bbb_j_m c2 variable).
If any of these strings were identified within the resource of any page visited by the 3ve.2 botnet, the respective resources (HTML or JS) wouldn’t be executed or rendered.
“For example, bbb_j_m contained strings from the White Ops JavaScript tag, and strings related to crypto-jacking such as Cryptonight, CoinHive, CryptonightWASMWrapper, and abortOnCannotGrowMemory”, says research from White Ops.
*The operation prevented crypto-jacking because it might lead to the detection of malware. If the user noticed that the computer is running slower, hotter, or noisier, it will lead to unwanted attention.
How Can You Prevent Your Sites From Ad Fraud?
- Create an Ads.txt file.
- Block Botnet & Fraudulent traffic.
- Implement Dynamic and adaptive IVT technology.
- Tie-up with ad fraud detection partners.
– Ads.txt
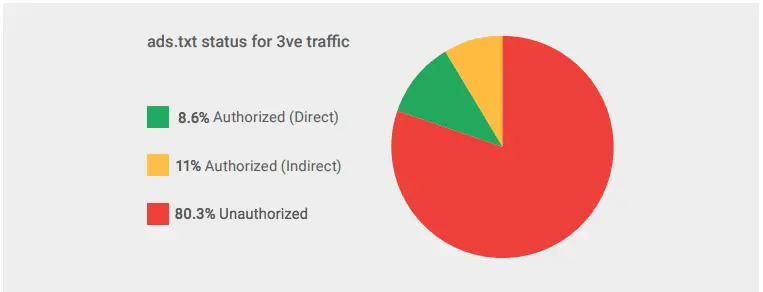
Sounds simple? The final research says that more than 80% of the ad requests generated by the 3ve operation were unauthorized. This means the publishers didn’t list the seller as authorized in their ads.txt file. If the ad exchanges stopped buying from unauthorized sellers, 80% of the fraud operation would have been stopped.
- If you don’t have an ads.txt file, create one right away.
- Update the ads.txt file regularly and look out for the errors using an ads.txt validator.
- Enforce the ad exchanges and buyers to buy only from authorized sellers.
– Traffic acquisition
It’s common to spend on acquiring traffic from legible social media sites and search forums. But don’t fall for the quixotic promises. High viewability, engagement, but lower acquisition costs? It’s probably a botnet or fraudulent traffic.
Scrutinize your acquisition channels and make informed decisions.
– Dynamic and adaptive IVT technology
3ve scheme churned 40,000 IPs every day and avoided detection tags. This pushes us to go beyond ordinary fraud detection systems. SSPs and DSPs with dynamic and adaptive IVT filters in addition to anomaly-based detection will ensure you’re being protected.
It’s time for us to implement a layered approach where in-house technology acts as the last line of defense.
– Proactive ad fraud detection partners
Last but not least, make sure your SSP has a dedicated team and technology either 3rd party or proprietary, to prevent and notice you of IVT or unauthorized selling. For instance, we have partnered with 3rd parties to make sure publishers we work with, are protected from ad fraudsters and spoofers.